| 区块链上基于云辅助的密文策略属性基数据共享加密方案 |
| |
| 引用本文: | 牛淑芬, 杨平平, 谢亚亚, 杜小妮. 区块链上基于云辅助的密文策略属性基数据共享加密方案[J]. 电子与信息学报, 2021, 43(7): 1864-1871. doi: 10.11999/JEIT200124 |
| |
| 作者姓名: | 牛淑芬 杨平平 谢亚亚 杜小妮 |
| |
| 作者单位: | 1.西北师范大学计算机科学与工程学院 兰州 730070;;2.西北师范大学数学与统计学院 兰州 730070 |
| |
| 基金项目: | 国家自然科学基金(61562077, 61662069, 61662071, 61772022),西北师范大学青年教师科研提升计划(NWNU-LKQN-13-12) |
| |
| 摘 要: | 
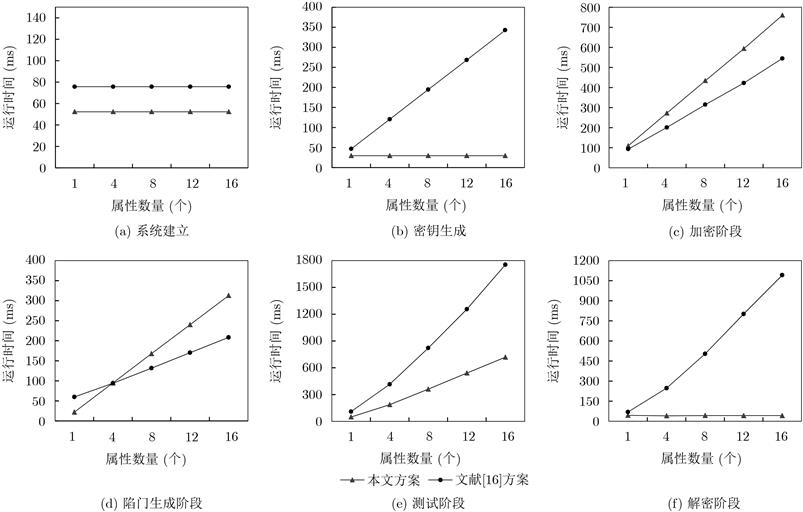
针对云存储的集中化带来的数据安全和隐私保护问题,该文提出一种区块链上基于云辅助的密文策略属性基(CP-ABE)数据共享加密方案.该方案采用基于属性加密技术对加密数据文件的对称密钥进行加密,并上传到云服务器,实现了数据安全以及细粒度访问控制;采用可搜索加密技术对关键字进行加密,并将关键字密文上传到区块链(BC)中,由区块.
..
|
| 关 键 词: | 区块链 属性基加密 可搜索加密 细粒度访问控制 |
| 收稿时间: | 2020-02-21 |
| 修稿时间: | 2020-12-08 |
|
| 点击此处可从《电子与信息学报》浏览原始摘要信息 |
|
点击此处可从《电子与信息学报》下载免费的PDF全文 |
|



